



Security Assertion Markup Language (SAML) is an open standard for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider. Using SAML you can enable Single Sign Ons for the following portals:
If Okta SSO configuration is done for the End Users, the End Users can access the SUMMIT application in any of the following ways:
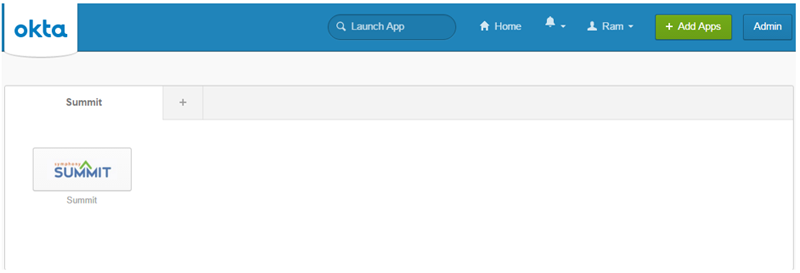
Figure: Accessing the SUMMIT application from OKTA URL
Figure: Logging into SUMMIT application

Figure: OKTA icon on SUMMIT Login page
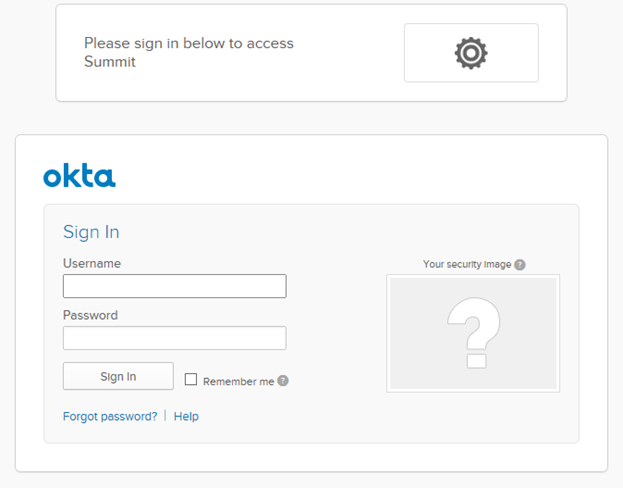
Figure: OKTA Login page

Figure: Logging into SUMMIT application
Note: If only Okta
is configured, on accessing the SUMMIT URL, you are automatically
redirected to the Okta URL and on providing Okta credentials,
you are logged into the SUMMIT application.
  See
Screen Shots See
Screen Shots
Figure: OKTA Login page
Figure: Logging into SUMMIT application
|
You can add SUMMIT as SAML app from the OKTA Console.
Log into OKTA Admin Console. Click Admin. Click Add Applications under Shortcuts menu.

Figure: Okta page: Adding SUMMIT app
Click Create a new app. The Create a New Application Integration pop-up is displayed. Select the SAML 2.0 option and click Create.
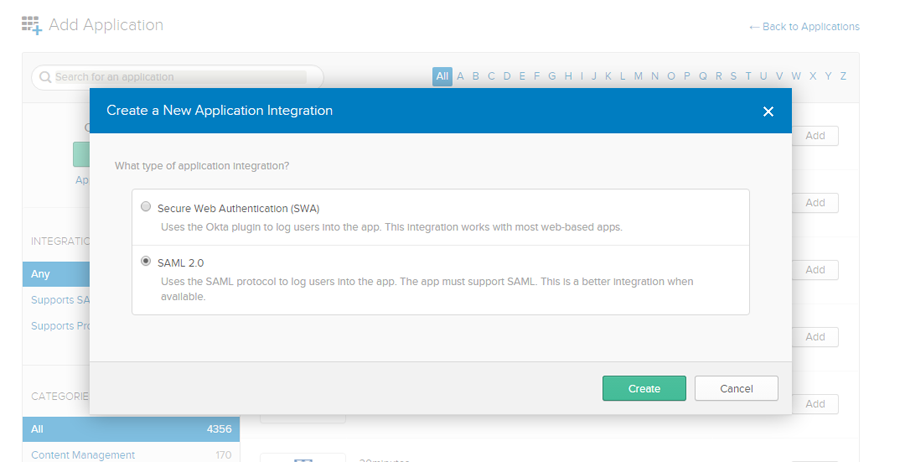
Figure: Okta page: SUMMIT app integration
Provide the required details under the General Settings and click Next.
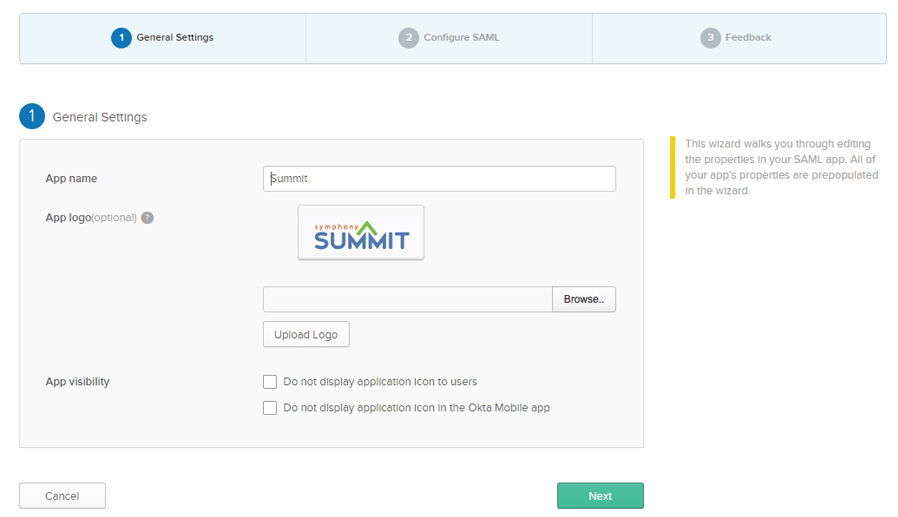
Figure: Okta page: SUMMIT app details
Provide the SAML details under SAML Settings and click Next.
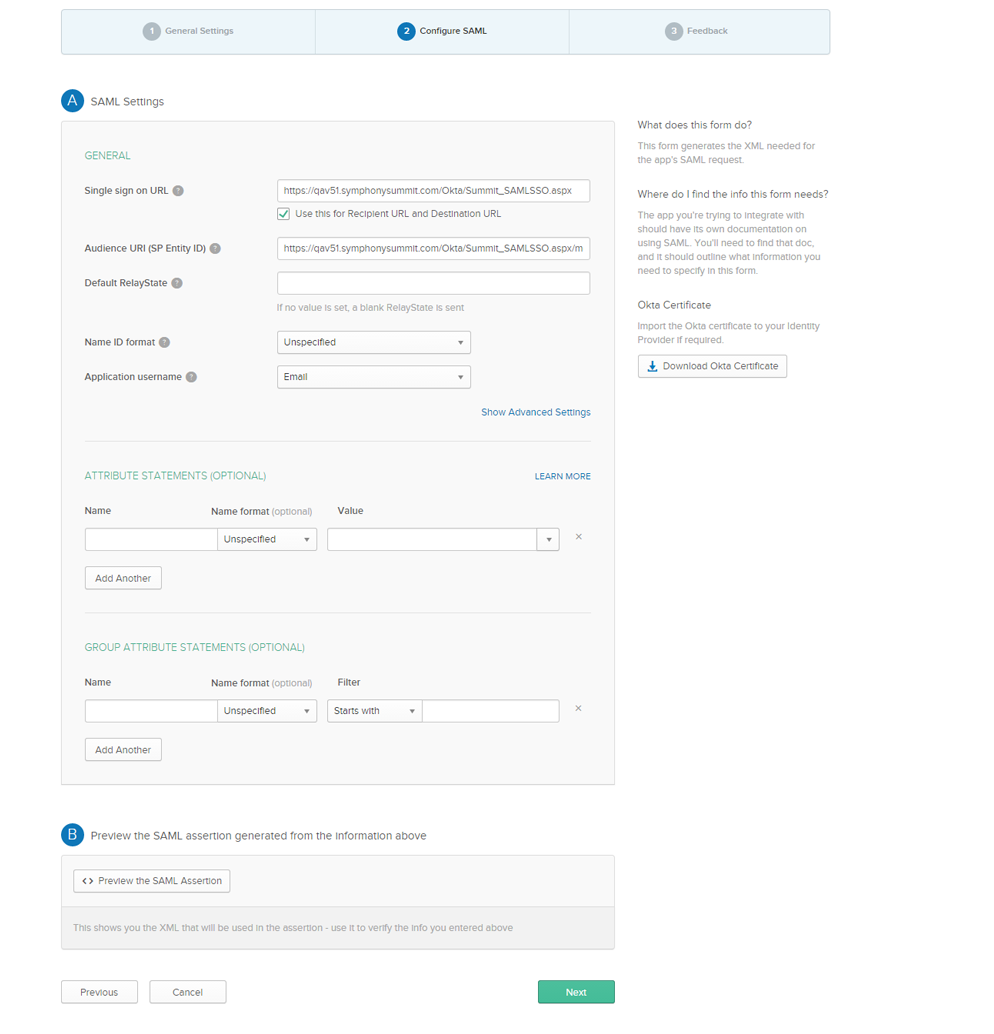
Figure: Okta page: SUMMIT SAML details
Provide the feedback details under Feedback and click Finish.
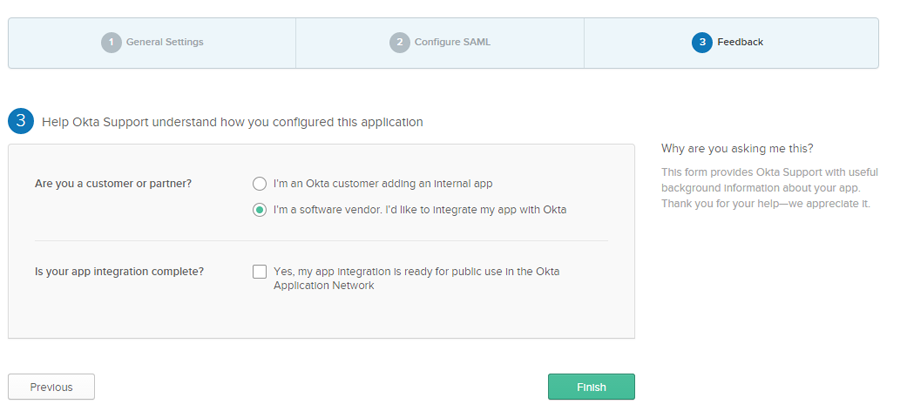
Figure: Okta page: Feedback
Click View Setup Instructions. Provide the required details.

Figure: Okta setup instructions

 Updating
SUMMIT Details as SAML App
Updating
SUMMIT Details as SAML App
If SUMMIT is already added as a SAML app, you can modify the details as required.
Log into OKTA Admin Console. Click Admin. Click Add Applications under Shortcuts menu.

Figure: Okta page: Editing SUMMIT app details
Click Apps you created. Select the SUMMIT app that you want to update and click Edit.
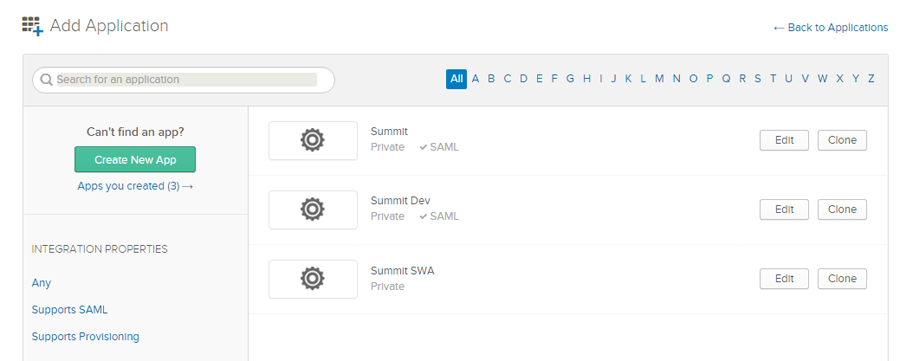
Figure: Okta page: Editing SUMMIT app details
Update the required details under the General Settings and click Next.

Figure: Okta page: Editing SUMMIT app details
Update the SAML details under SAML Settings and click Next.

Figure: Okta page: Editing Feedback details
Update the feedback details under Feedback and click Finish.

Figure: Okta page: Editing Feedback details
Click View Setup Instructions. Update the required details.

Figure: Okta page: Editing setup instructions

 Adding
User and Activating Them
Adding
User and Activating Them
You can add the users for whom SSO will be available for the SUMMIT SAML app.
Log into OKTA Admin Console. Click Admin. Select People from the Directory menu.
Figure: Adding People
Click Add Person. The Add Person pop-up is displayed. Provide the details about the user you are adding and click Add Person. If you want to add more users, click Save and Add Another.
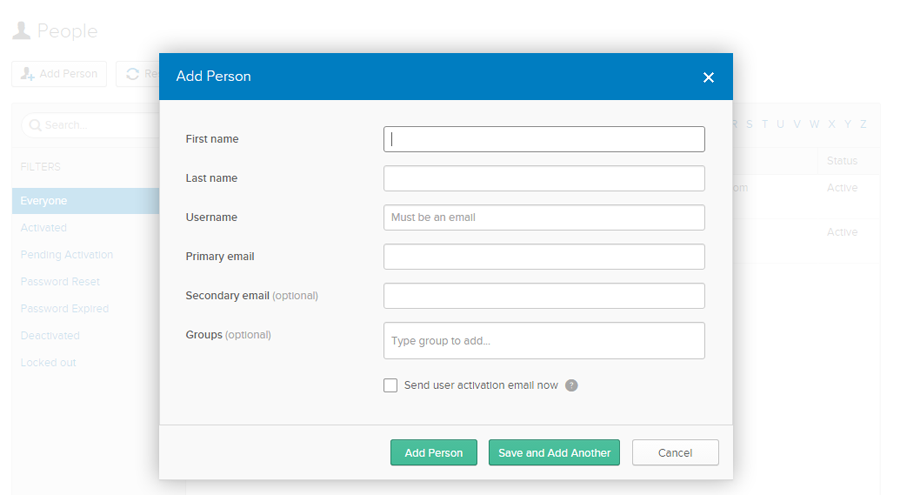
Figure: Adding People details
The added user needs to be activated so that the user can use SSO from OKTA for SUMMIT. Click Activate. A confirmation pop-up page is displayed. Click Activate User.
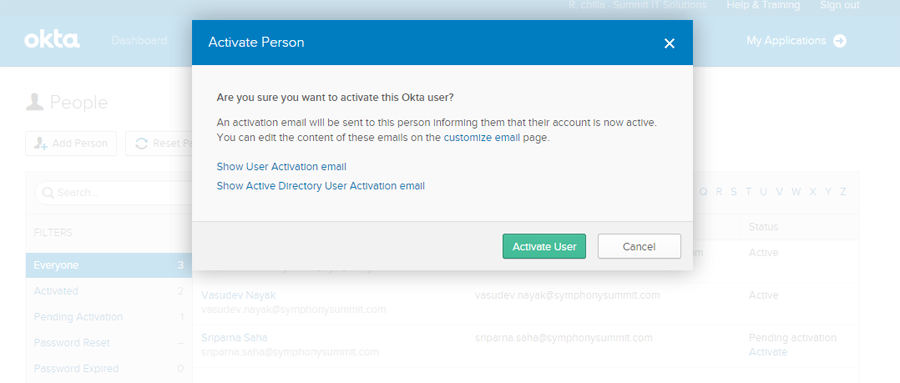
Figure: Activating the added person
To configure SSO in the SUMMIT application for Okta:
Select Admin > Basic > Infrastructure > SSO Configuration. The SSO CONFIGURATION page is displayed. Select SAML and click ADD NEW under ACTIONS panel.
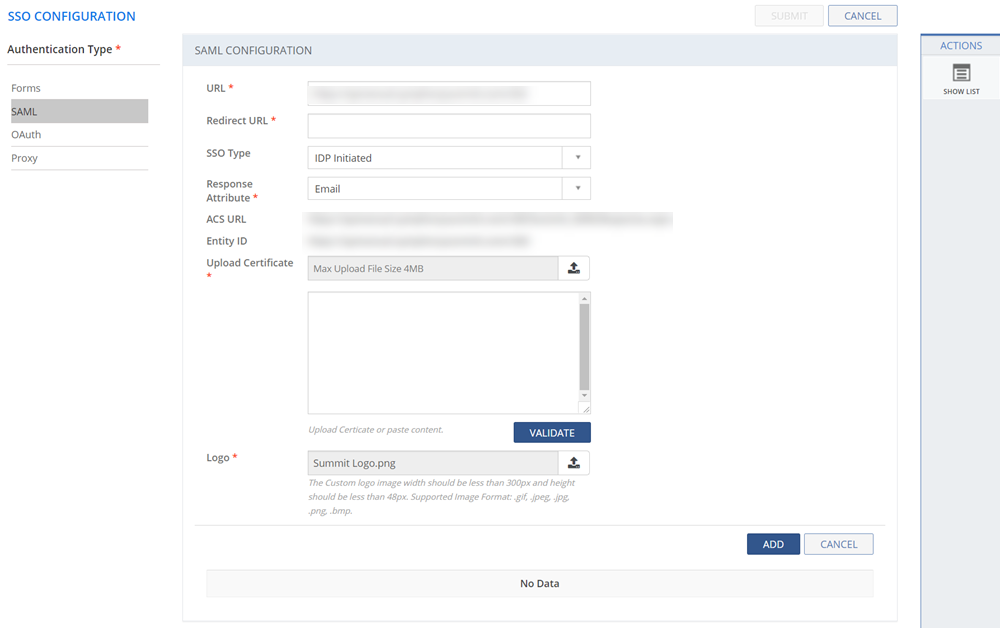
Figure: SSO Configuration page: Okta
Type in the SSO configuration details. For more information about the fields on the SSO CONFIGURATION page, see Field Description.
Click VALIDATE. The certificate information is displayed if the uploaded certificate is valid. For invalid certificate, an error message is displayed.
Click SUBMIT. The SSO is configured successfully.
The following table describes the fields on the SSO CONFIGURATION page:
| Field | Description |
| URL | Provide the URL. |
| Redirect URL | Copy the SSO URL details from Okta configuration page and paste the URL details in this text box. |
| SSO Type | Select the SSO Type from the drop-down list. |
| Response Attribute | Select the response attribute from the drop-down list. |
| Upload Certificate | Upload the certificate that you downloaded during the SSO configuration using Okta SAML apps. |
| Logo | Upload an image to be displayed as Google icon. |
You can add SUMMIT as SAML app from the Google Admin Console.
Log into Google Admin Console. Click Apps and select SAML Apps.
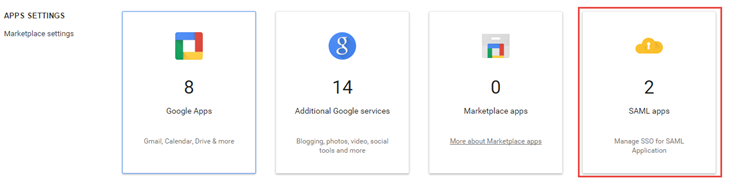
Figure: Google App Settings page
Click the Plus icon to enable SSO for SAML application. Click SETUP MY OWN CUSTOM APP.

Figure: Setting up SUMMIT as custom app
Provide the SSO URL, Entity ID, and download the certificate. Click NEXT.
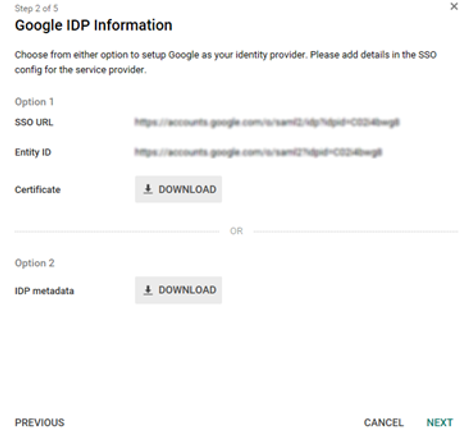
Figure: Downloading the certificates
Provide basic information about the SUMMIT application and click NEXT.
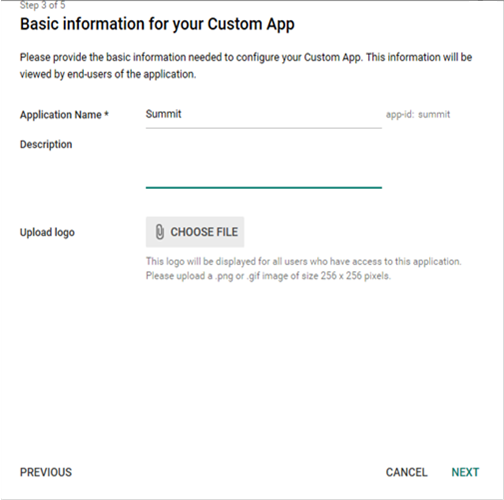
Figure: Basic details
Provide the Service Provider details and click NEXT.
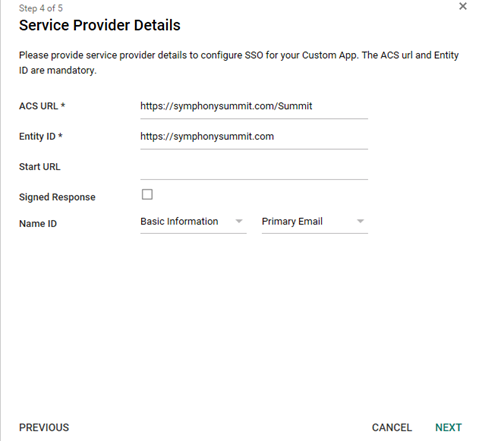
Figure: Service Provider details
Provide mappings between service provider attributes to available user profile fields. You can also come back later to complete the attribute mapping. Click FINISH.
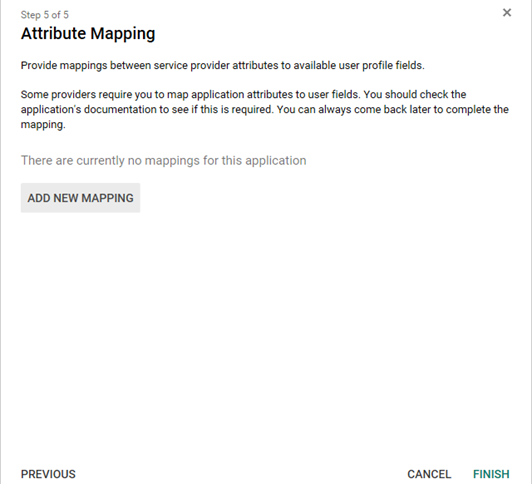
Figure: Attribute mapping

 Updating
SUMMIT Details as SAML App
Updating
SUMMIT Details as SAML App
If SUMMIT is already added a SAML app, you can modify the details as required.
Log into Google Admin Console. Click Apps and select SAML Apps.

Figure: Google App Settings page
Select the SUMMIT SAML app that you want to update.

Figure: Updating SUMMIT details
Figure: Updating SUMMIT details
Click the Service Provide Details and the Attribute Mapping sections to modify details in the respective sections.
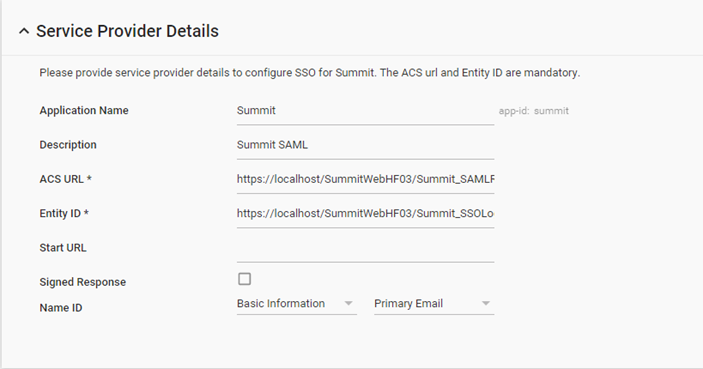
Figure: Updating Service Provider details

Figure: Updating Attribute Mapping

 Enabling/
Disabling the SUMMIT SAML App
Enabling/
Disabling the SUMMIT SAML App
You can enable or disable the SUMMIT SAMP app configuration for all the users or for selected organizations.
Log into Google Admin Console. Click Apps and select SAML Apps.

Figure: Google App Settings page
All the configured SAML apps are displayed. Click the three dots next to the SUMMIT SAML app that you want to enable or disable for users. Select the appropriate option from the options. The available options are ON for everyone, ON for some organizations, and OFF.

Figure: Enabling SUMMIT app
| Option | Description |
| ON for everyone | If selected, the SAML app is available to all the users. |
| ON for some organizations | If selected, the SAML app is available to users of the selected organizations |
| OFF | If selected, the SAML app is not available to anybody. |
You can add the users for whom SSO will be available for the SUMMIT SAML app.
Log into Google Admin Console and select Users from the left menu.
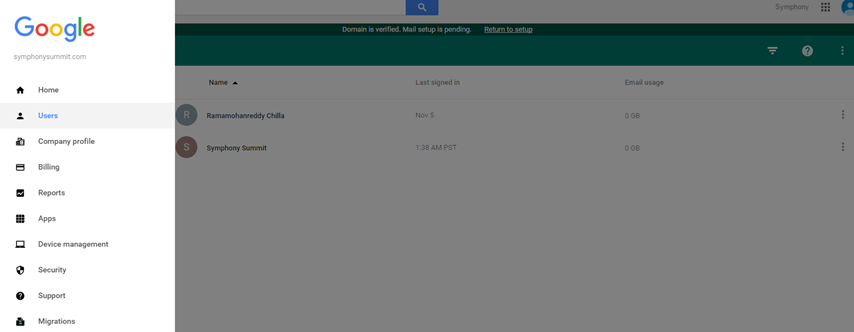
Figure: Adding Users
Mouse hover on the Add icon, The available icons are: Invite users, Add multiple users, and Add user.
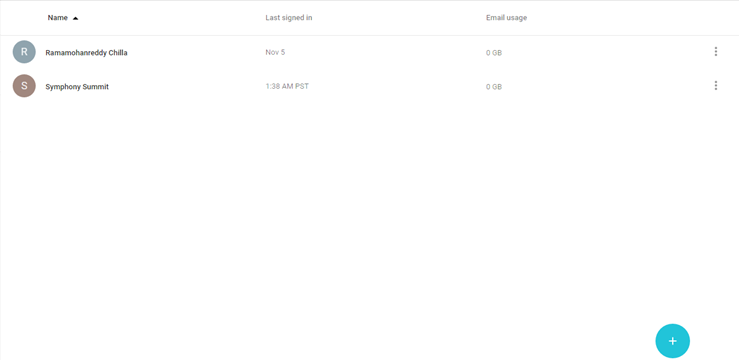
Figure: Adding users
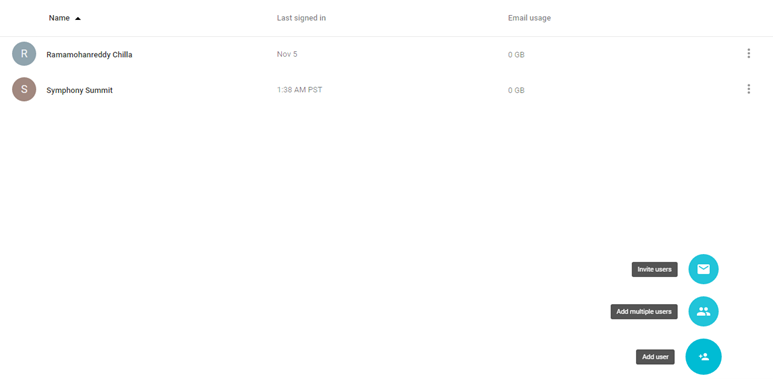
Figure: Multiple options to add users
Invite users: Select this option to invite users to use the SUMMIT SAML app as SSO from Google. Specify the e-mail ids of the users to whom you want to send the invitation.
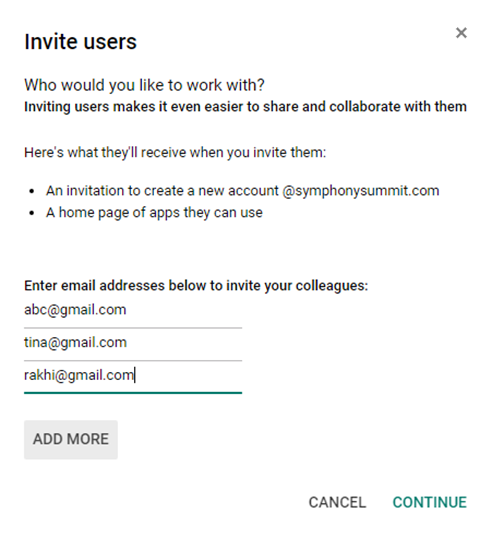
Figure: Inviting users
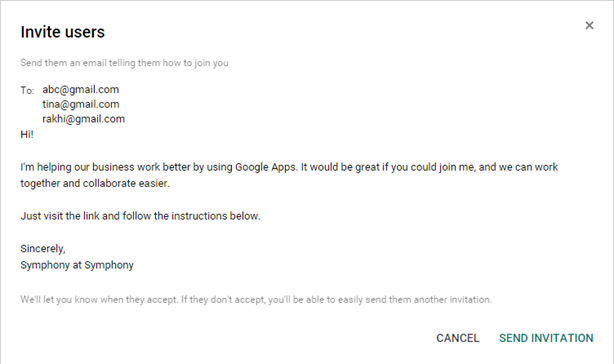
Figure: Inviting users
Add multiple users: Select this option to add multiple users. You can upload a Microsoft Excel sheet with the names of the users and other details (download the template AS.CSV).
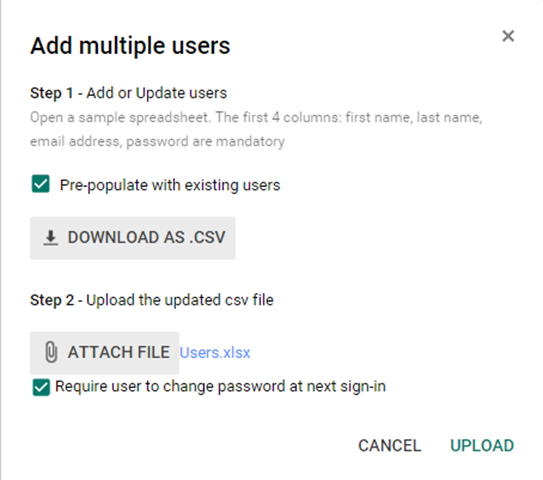
Figure: Adding multiple users
Add user: Select this option to a user. Provide the first name, last name, and the e-mail id of the user.
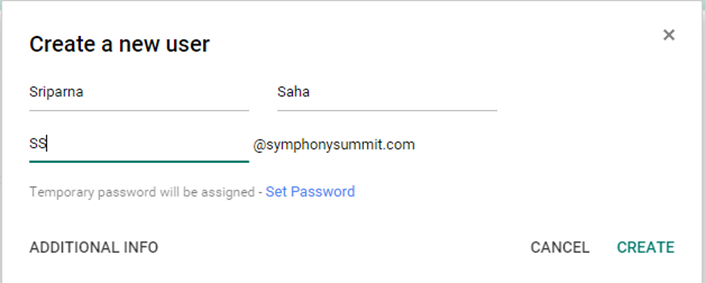
Figure: Adding single user
To configure SSO in the SUMMIT application for Google:
Select Admin > Basic > Infrastructure > SSO Configuration. The SSO CONFIGURATION page is displayed. Select SAML and click ADD NEW under ACTIONS panel.

Figure: SSO Configuration page
Type in the SSO configuration details. For more information about the fields on the SSO CONFIGURATION page, see Field Description.
Click VALIDATE. The certificate information is displayed if the uploaded certificate is valid. For invalid certificate, an error message is displayed.
Click SUBMIT. The SSO is configured successfully.
The following table describes the fields on the SSO CONFIGURATION page:
| Field | Description |
| URL | Provide the URL. |
| Redirect URL | Copy the SSO URL details from Google configuration page and paste the URL details in this text box. |
| SSO Type | Select the SSO Type from the drop-down list. |
| Response Attribute | Select the response attribute from the drop-down list. |
| Upload Certificate | Upload the certificate that you downloaded during the SSO configuration using Google SAML apps. |
| Logo | Upload an image to be displayed as Google icon. |

 Prerequisites
to be performed in Ping Federate Server
Prerequisites
to be performed in Ping Federate Server
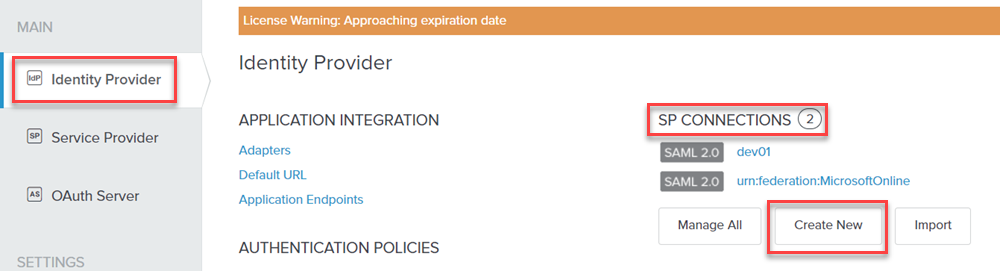
On the SP Connection section, configure the tabs as follows:
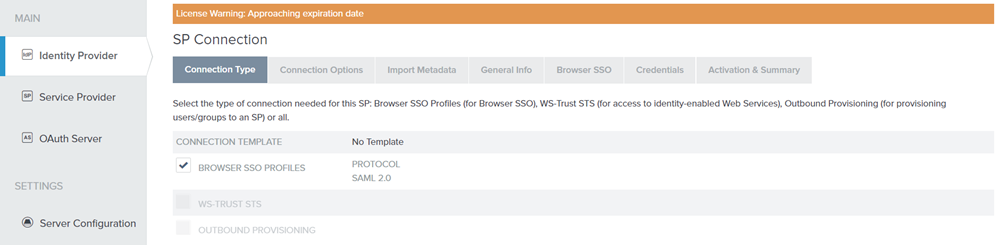
Figure: SP Connection _ Connection Type
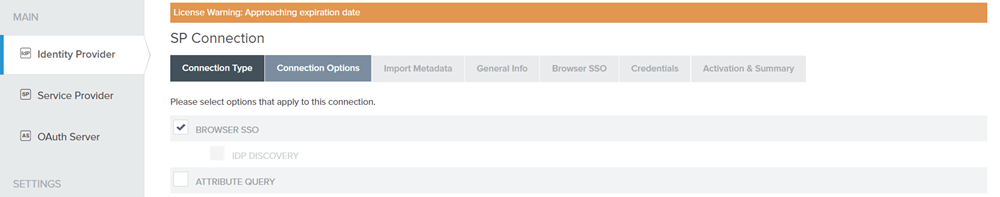
Figure: SP Connection _ Connection Options
If you have a Metadata URL or FILE, select the respective options and provide the information. If you do not have an URL or a FILE, Select NONE.
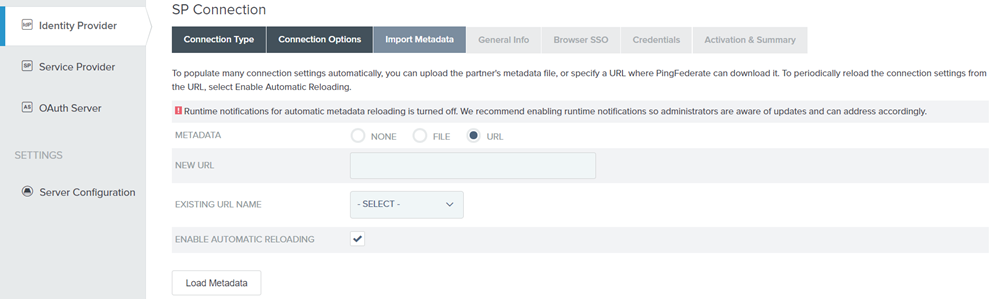
Figure: SP Connection _ Import Metadata
On the General Info tab, specify the PARTNER'S ENTITY ID, CONNECTION NAME, and the BASE URL. Select the LOGGING MODE as STANDARD.
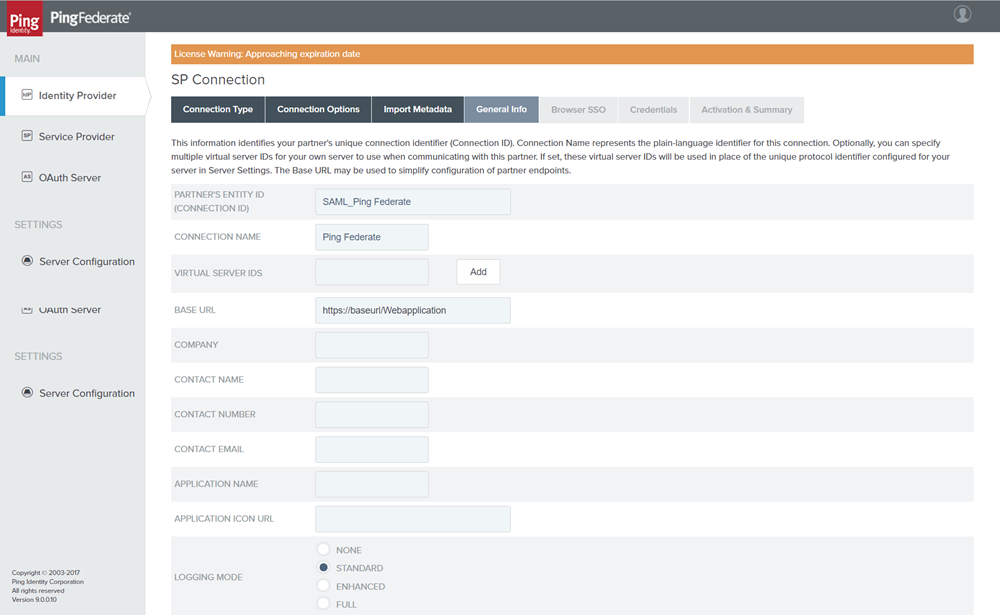
Figure: SP Connection _ General Info
On the Browse SSO tab, click Configure Browse SSO.
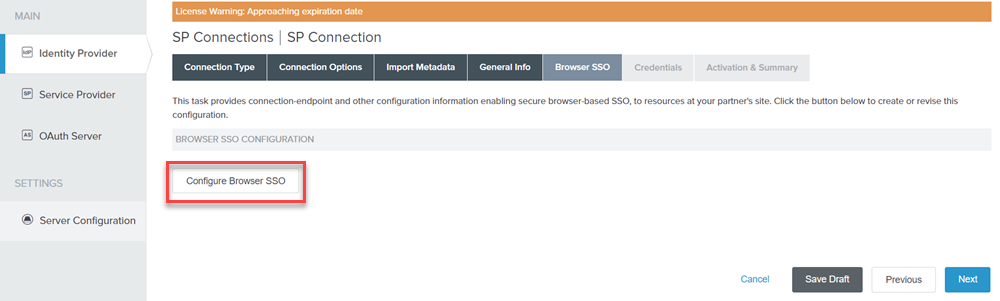
Figure: SP Connection _ Browse SSO
On the SAML Profiles section, select IDP-INITAIATED SSO.
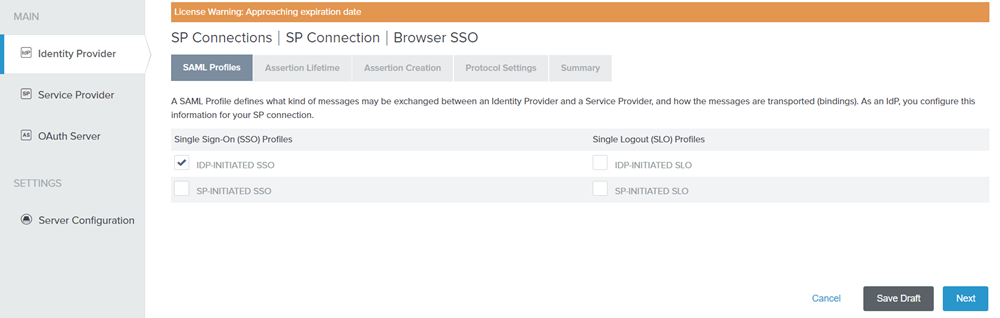
Figure: SAML PROFILES
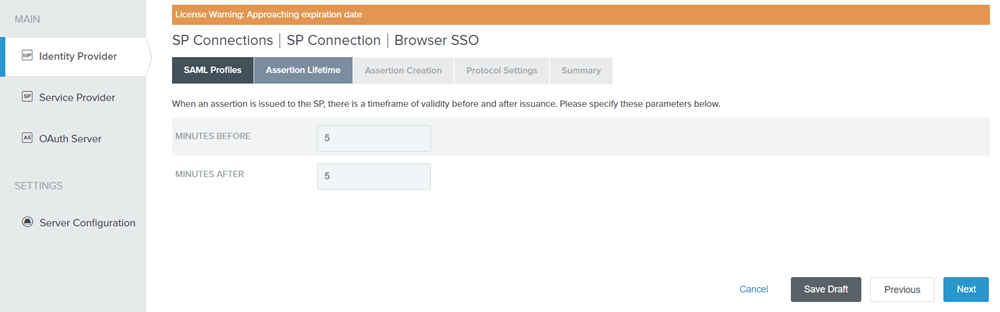
Figure: Assertion Lifetime tab
On the Assertion Creation tab, click Configure Assertion Creation.
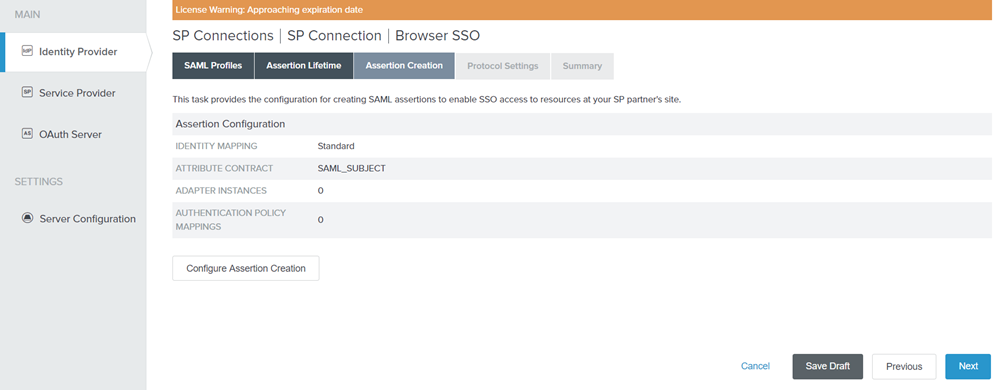
Figure: Configure Assertion
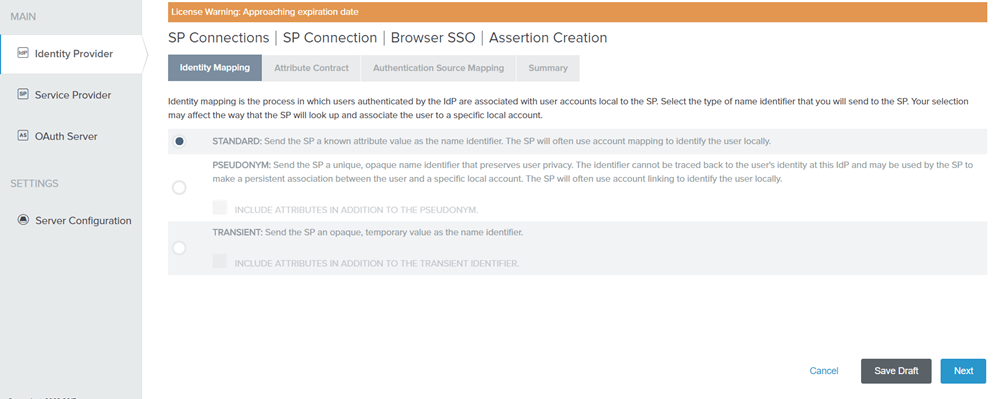
Figure: Identity Mapping
On the Attribute Contract tab, click Add under Extend the Contract.
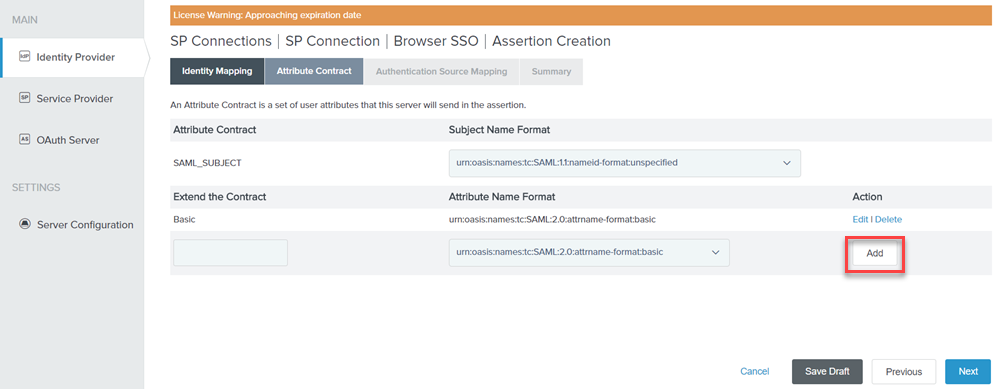
Figure: Attribute Contract
On the Authentication Source Mapping tab, click Map New Adapter Instance.
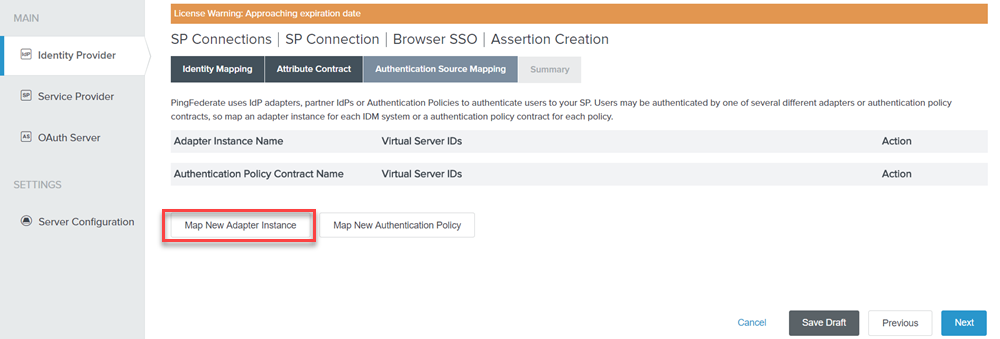
Figure: Authentication Source Mapping
On the Adapter Instance tab, select ADAPTER INSTANCE as HTML Form Adapter.
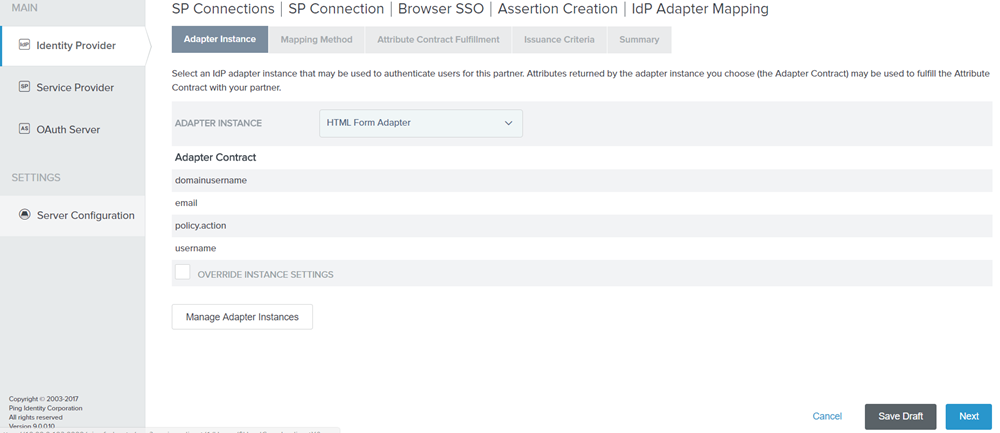
Figure: Adapter Instance
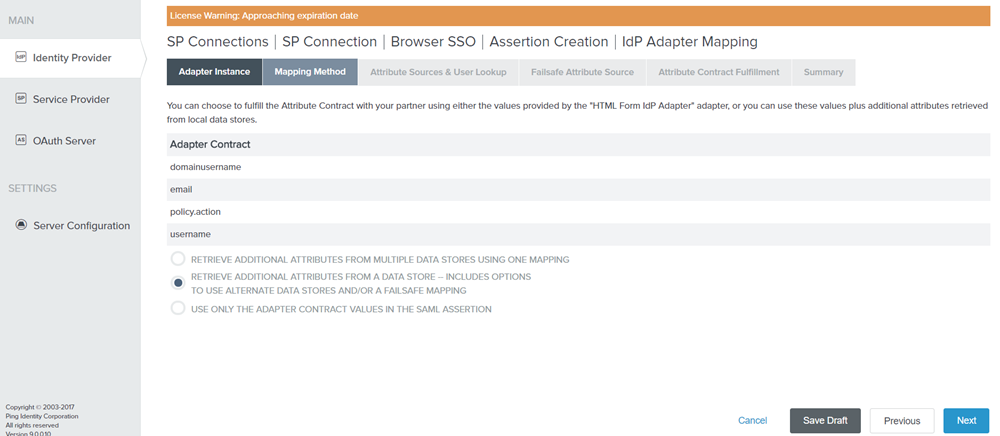
Figure: Mapping Method

 Attribute Sources
& User Lookup
Attribute Sources
& User Lookup
Click Add Attribute Source.
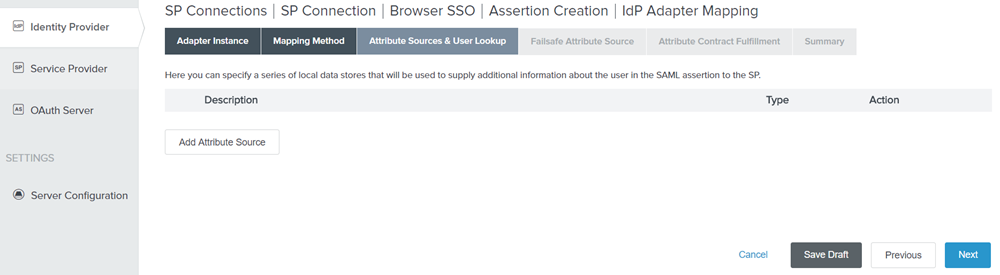
Figure: Attribute Source
Note: Click Manage Data Stores to configure the Active Data Store.

Figure: Data Source
Specify the Base DN
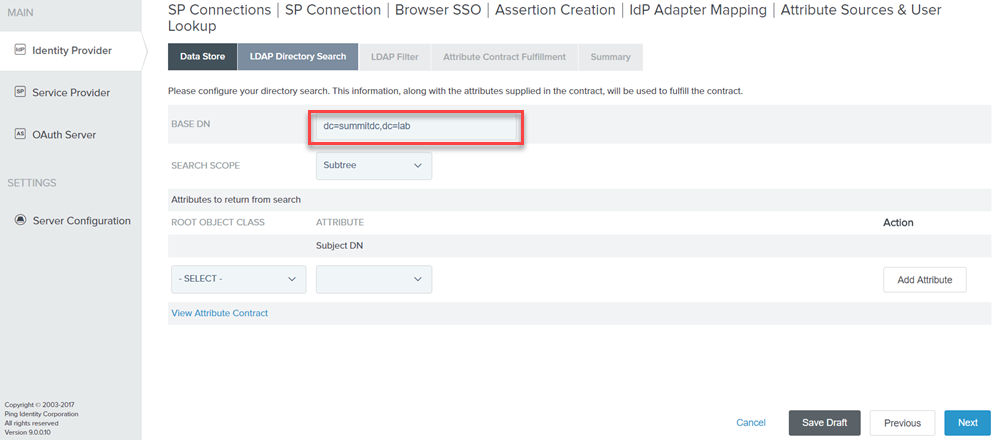
Figure: LDAP Directory Search
Specify the Filter as (sAMAccountName=${username})
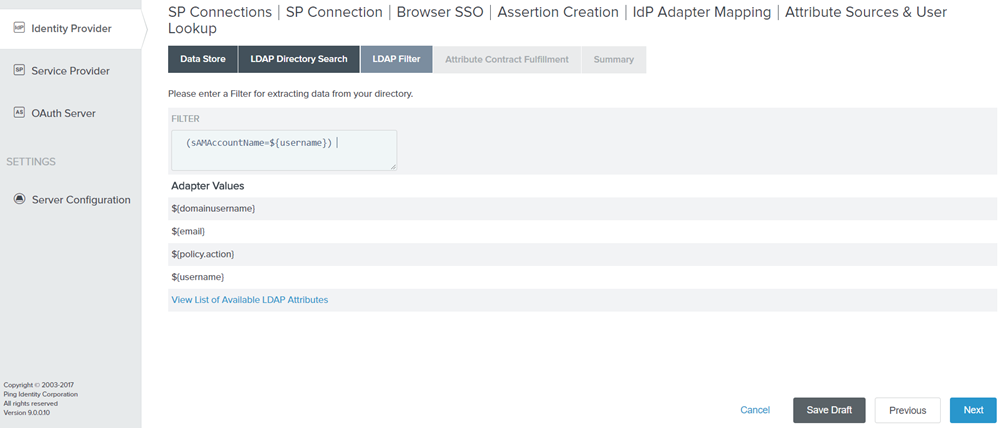
Figure: LDAP Filter

 Attribute
Contract Fulfillment
Attribute
Contract Fulfillment
Select the Source as Adapter and Value as Username.
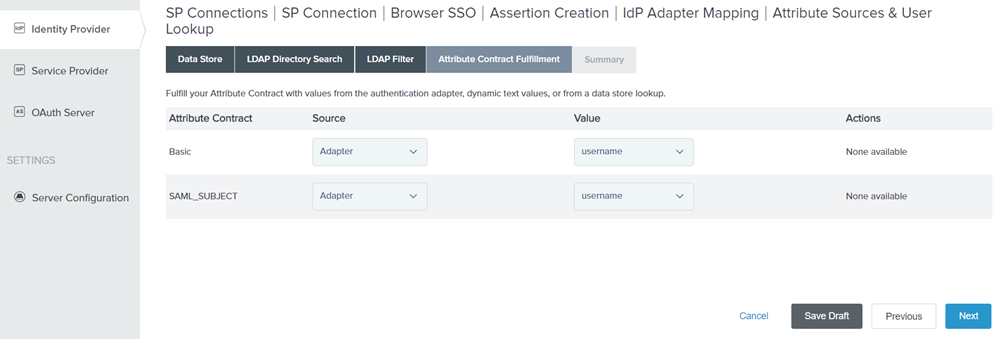
Figure: Attribute Contract Fulfillment
On the Summary page, click Done. You will be redirected to Attribute Sources & User Lookup tab.
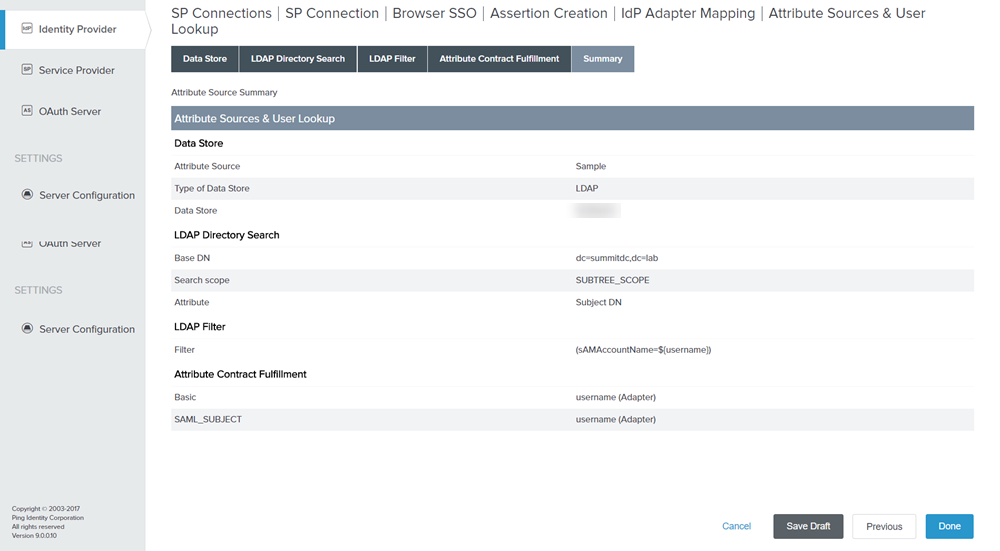
Figure: Summary
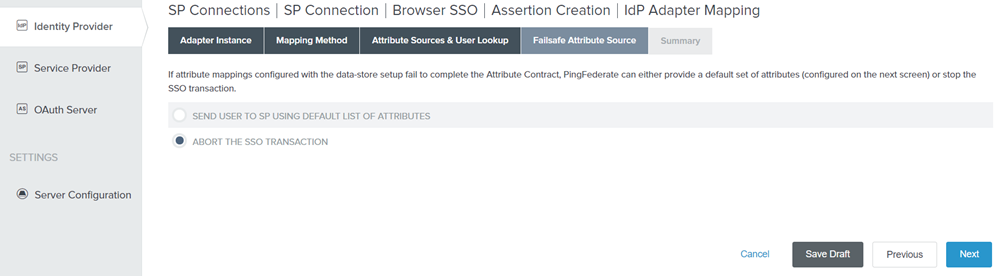
Figure: Failsafe Attribute Source
On the Summary tab, click Done. You will be redirected to Assertion Creation tab.
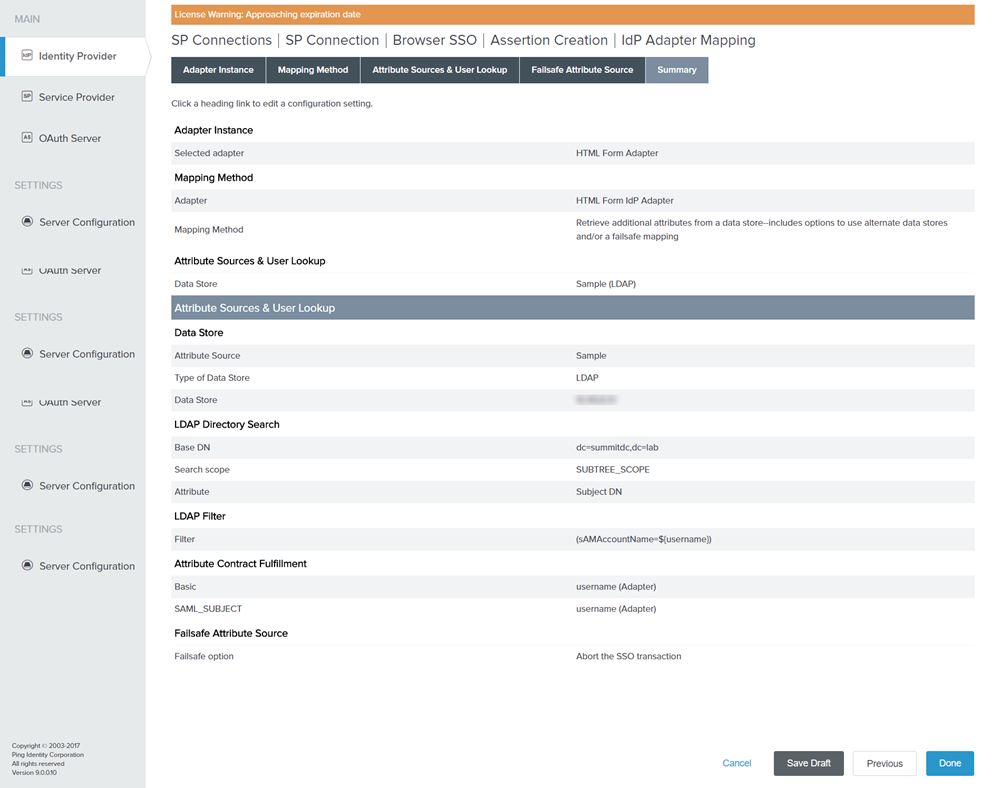
Figure: Summary
On the Summary tab, click Done. You will be redirected to Browser SSO tab.
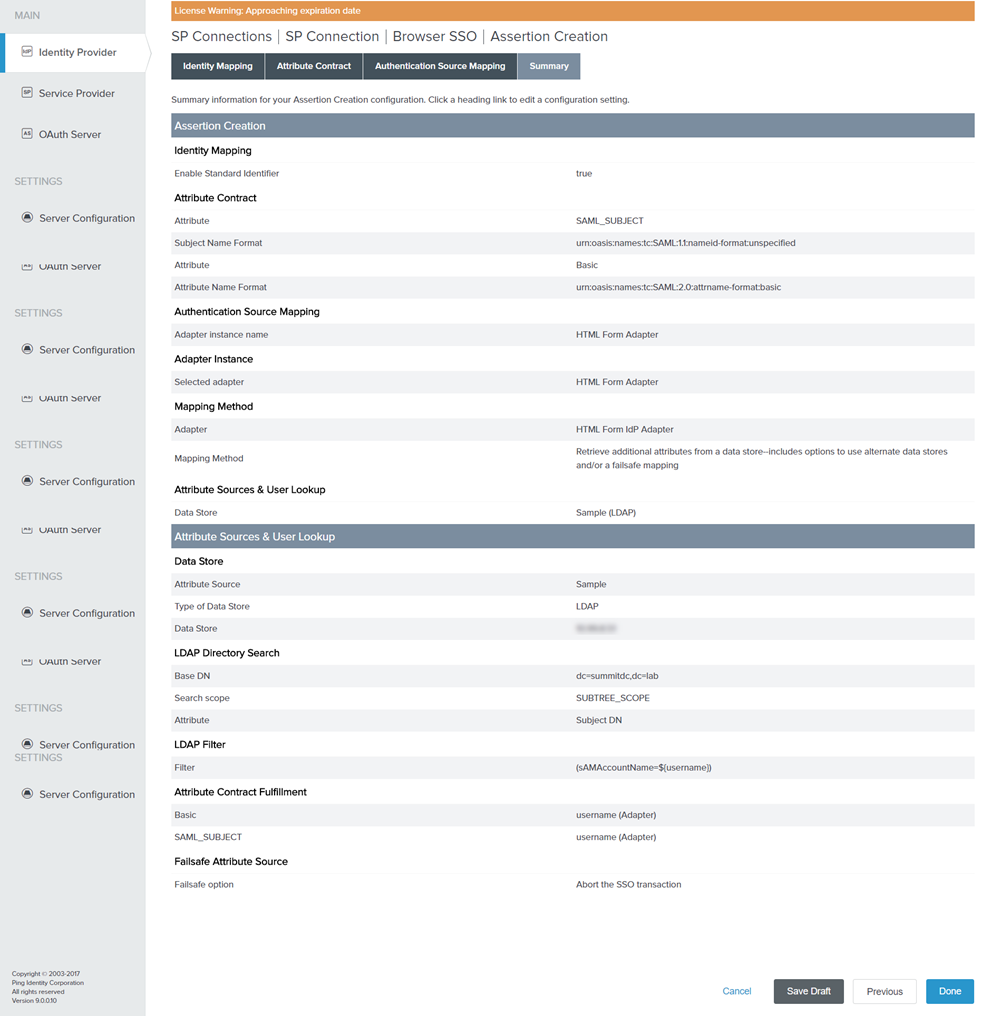
Figure: Summary tab
On the Protocol Settings tab, click Configure Protocol Settings.

Figure: Protocol Settings tab

 Assertion Consumer Service
URL
Assertion Consumer Service
URL
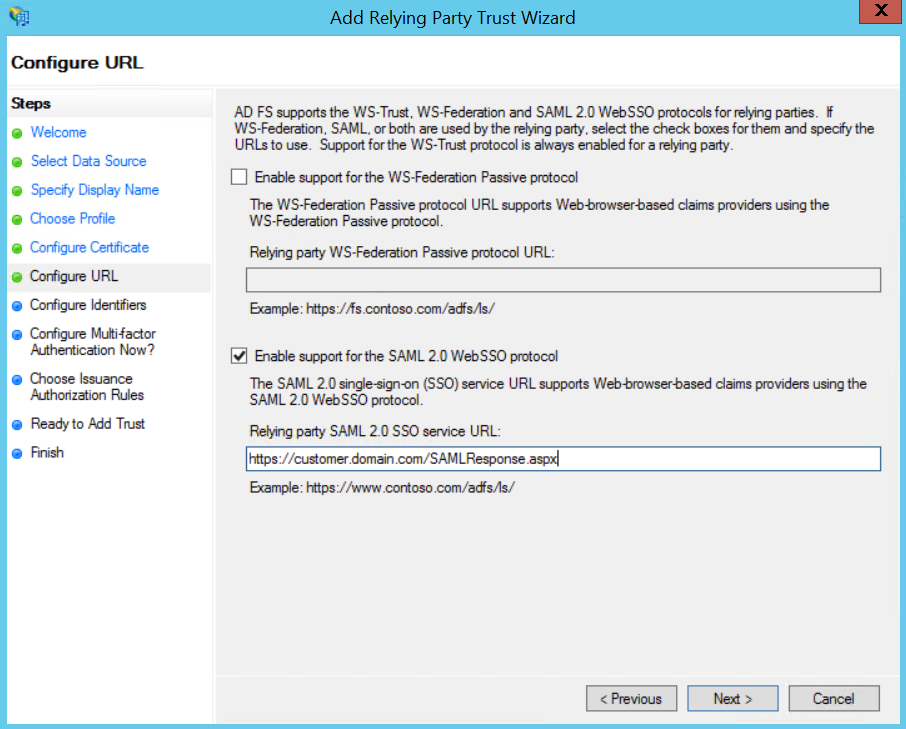
Select Binding as POST and specify the Endpoint URL as /Summit_SAMLResponse.aspx.
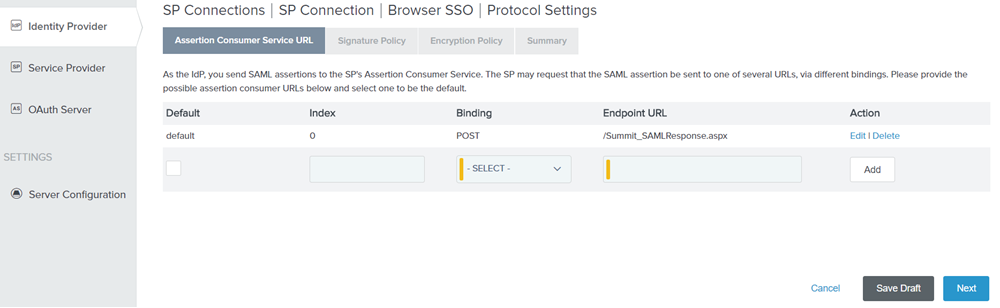
Figure: Assertion Consumer Service URL
Select ALWAYS SIGN THE SAML ASSERTION and click Next.
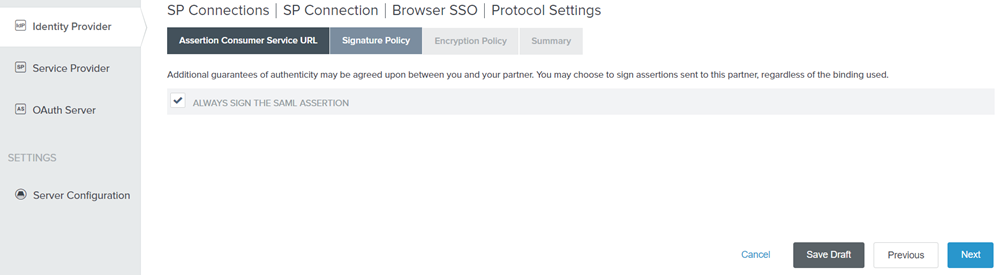
Figure: Signature Policy
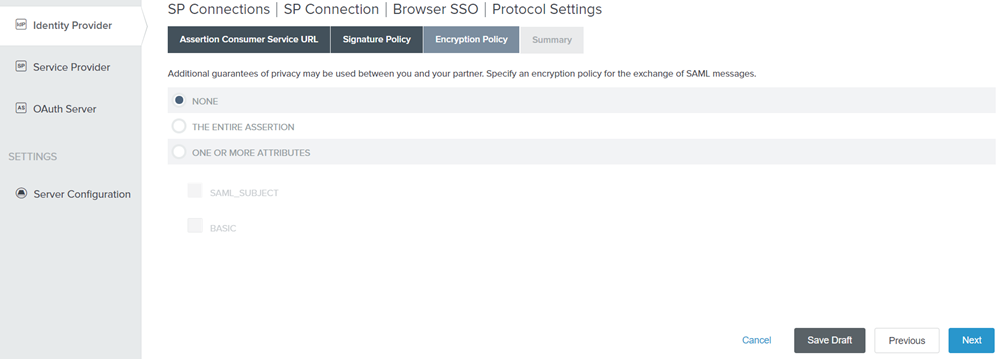
Figure: Encryption Policy
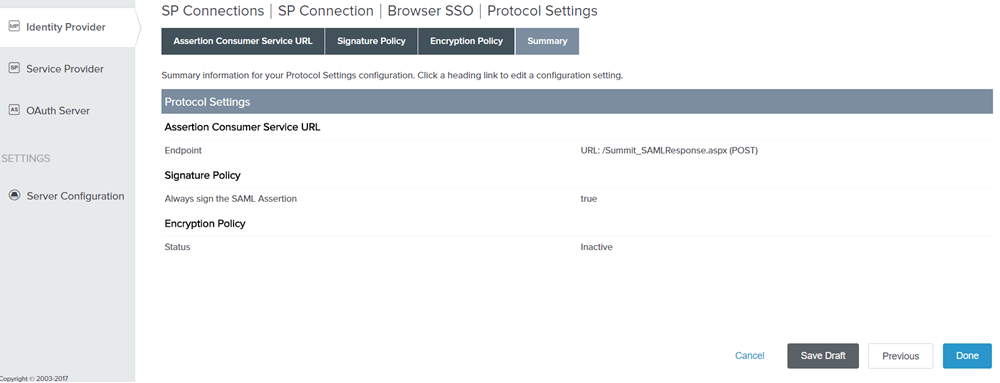
Figure: Summary
On the Summary tab, click Done. You will redirected to SP Connection Page.
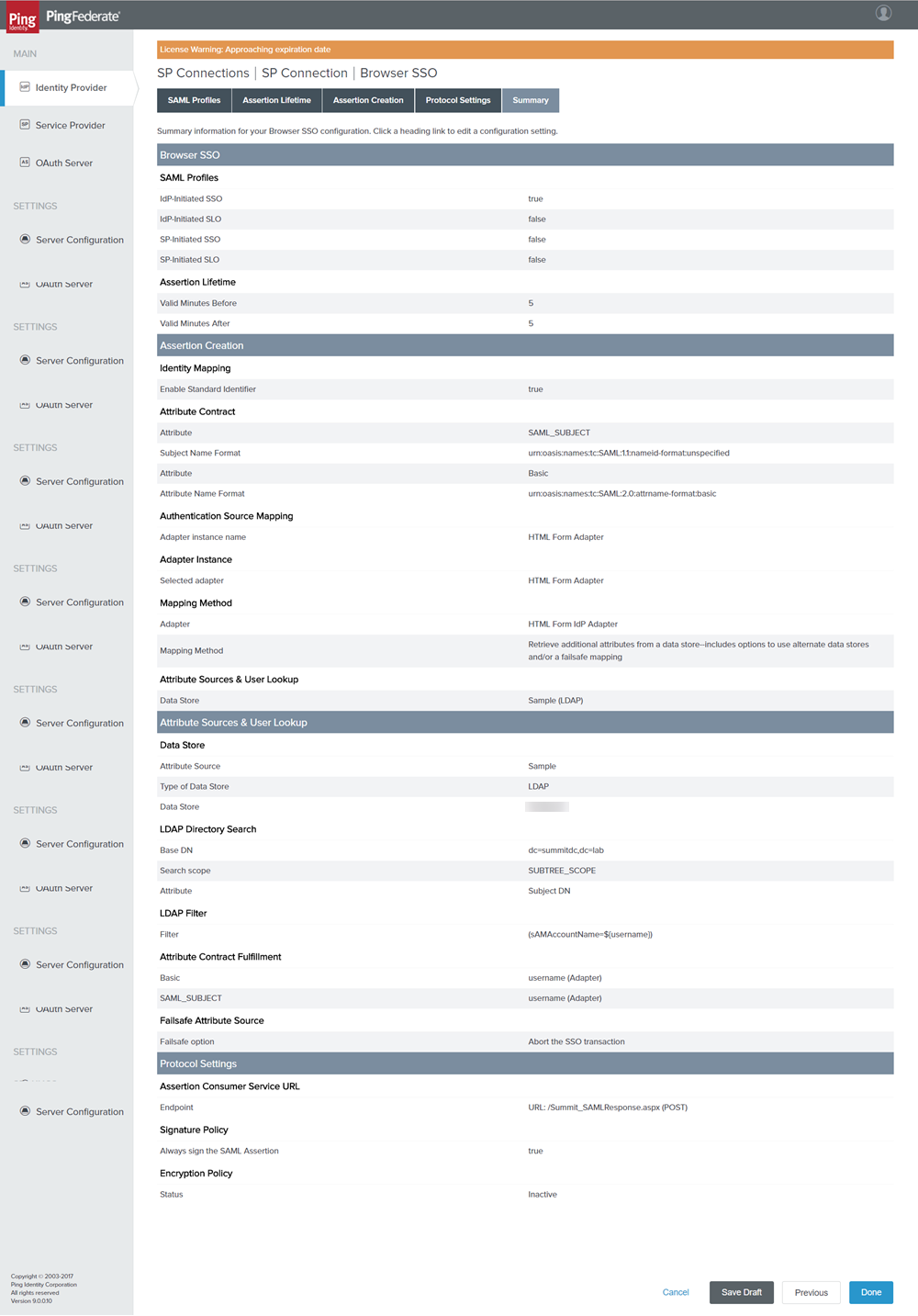
Figure: Browser SSO _ Summary
Click Configure Credentials.
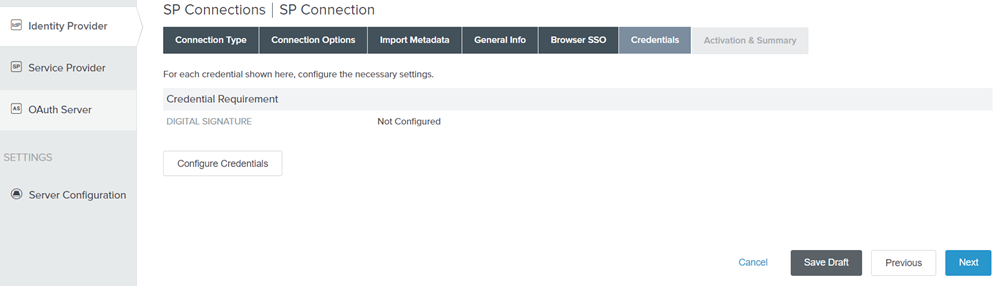
Figure: Credentials
Click Manage Certificates and configure Signing Certificate.
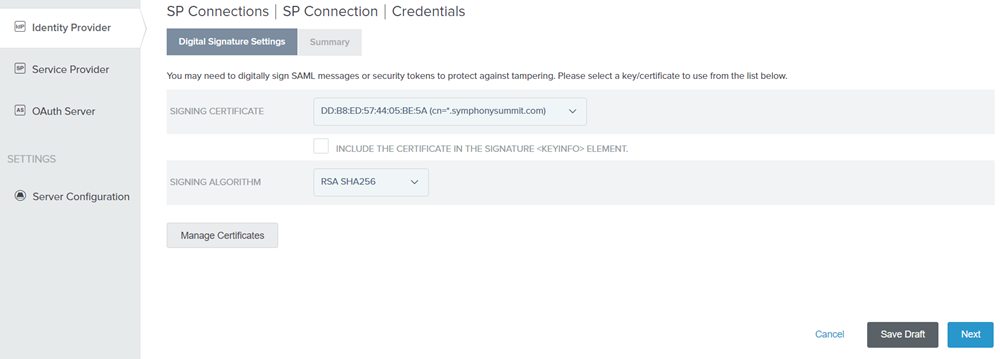
Figure: Digital Signature Settings
On the Summary tab, click Done. You will be redirected to SP Connection page.
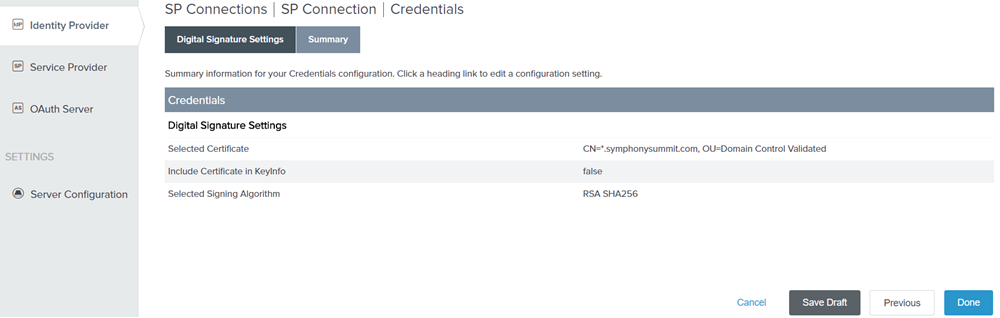
Figure: Credentials Summary
Select the Connection Status as Active and click Save.
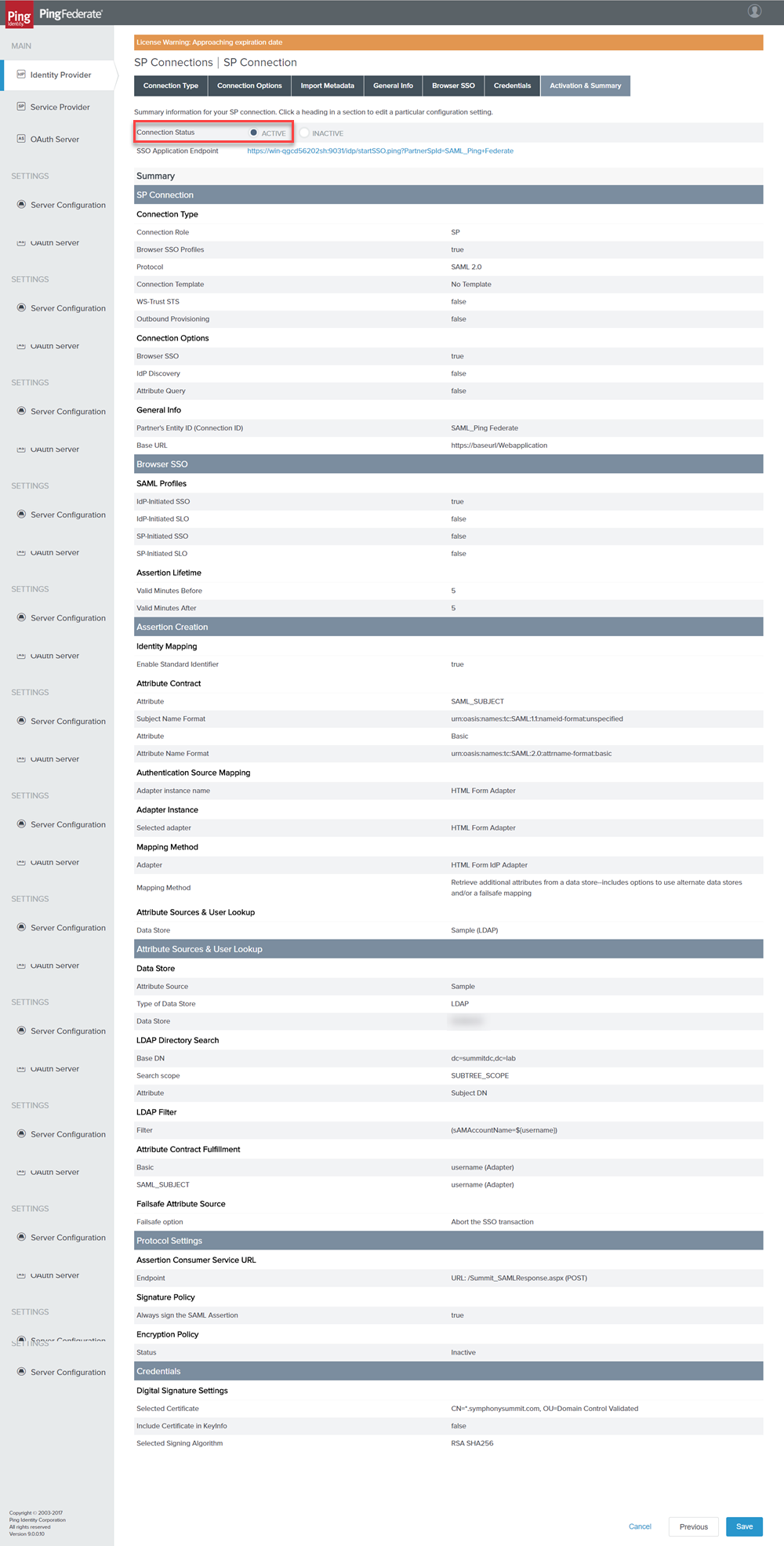
Figure: SP Connection _ Summary
Click Server Configuration and then click Metadata Export under ADMINISTRATIVE FUNCTIONS.
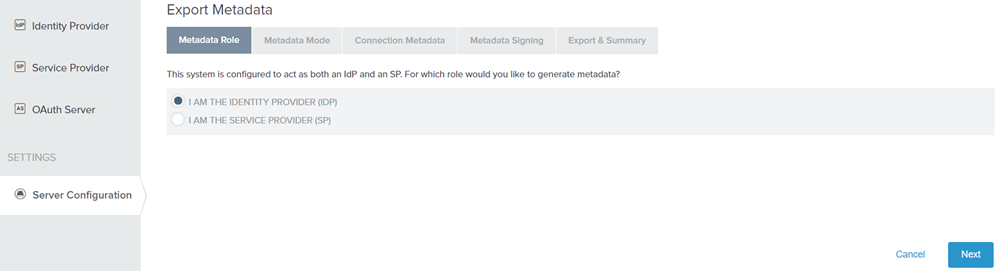
Figure: Metadata Role
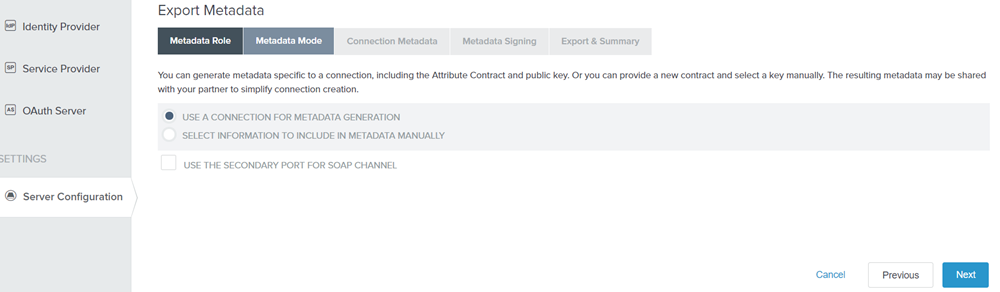
Figure: Metadata Mode
Select the configured SP Connection from the drop-down list.
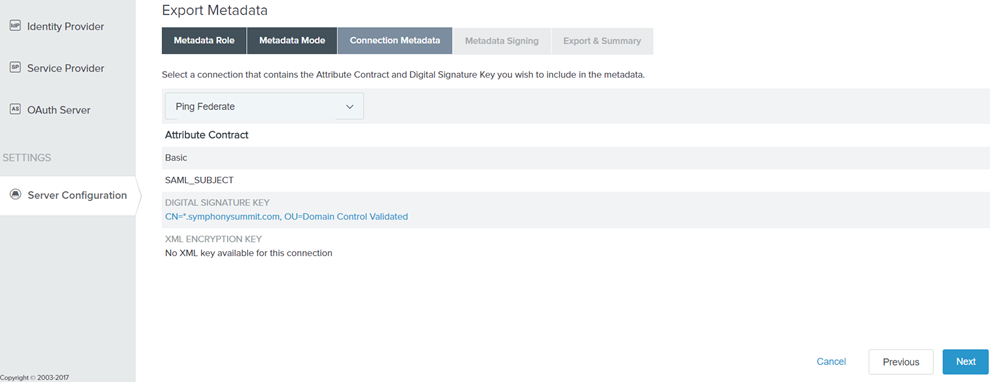
Figure: Connection Metadata
Select the Signing Certificate from the drop-down list.
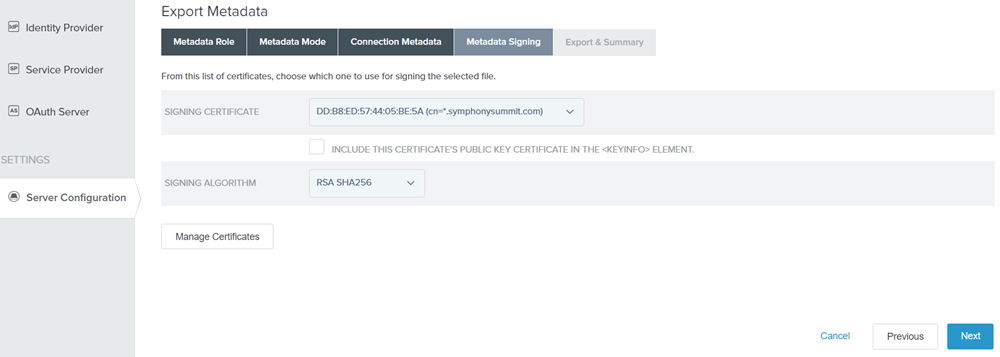
Figure: Metadata Signing
On the Export & Summary tab, click Export and then click Done. An XML file is downloaded.
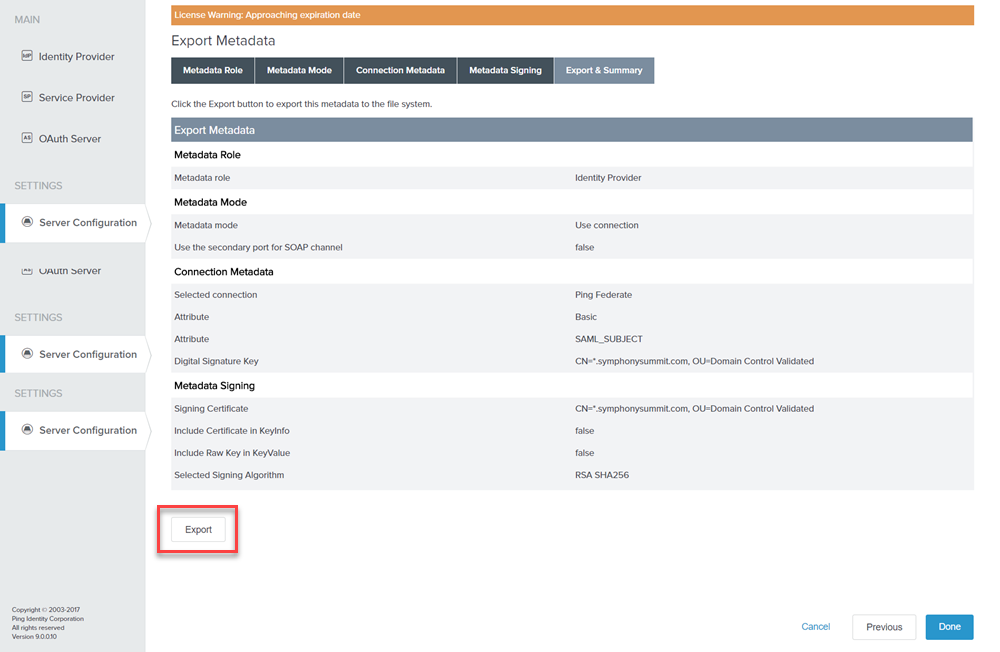
Figure: Export & Summary
Note:
|

 Configuration
in SUMMIT Application
Configuration
in SUMMIT Application
To configure SSO in the SUMMIT application:
Select Admin > Basic > Infrastructure > SSO Configuration. The SSO CONFIGURATION page is displayed. Select SAML and click ADD NEW under ACTIONS panel.

Figure: SSO Configuration page
Type in the SSO configuration details. For more information about the fields on the SSO CONFIGURATION page, see Field Description.
Click VALIDATE. The certificate information is displayed if the uploaded certificate is valid. For invalid certificate, an error message is displayed.
Click SUBMIT. The SSO is configured successfully.
The following table describes the fields on the SSO CONFIGURATION page:
| Field | Description |
| URL | Provide the URL. |
| Redirect URL | Copy the SSO URL details from Ping Federate configuration page and paste the URL details in this text box. |
| SSO Type | Select the SSO Type from the drop-down list. |
| Response Attribute | Select the response attribute from the drop-down list. |
| Upload Certificate | Upload the certificate that you downloaded during the SSO configuration using Ping Federate SAML apps. |
| Logo | Upload an image to be displayed as Ping Federate icon. |

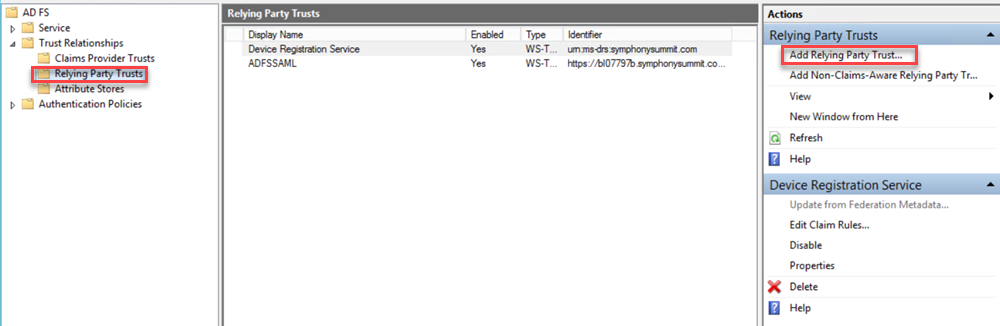
 Prerequisites
to performed in ADFS
Prerequisites
to performed in ADFS

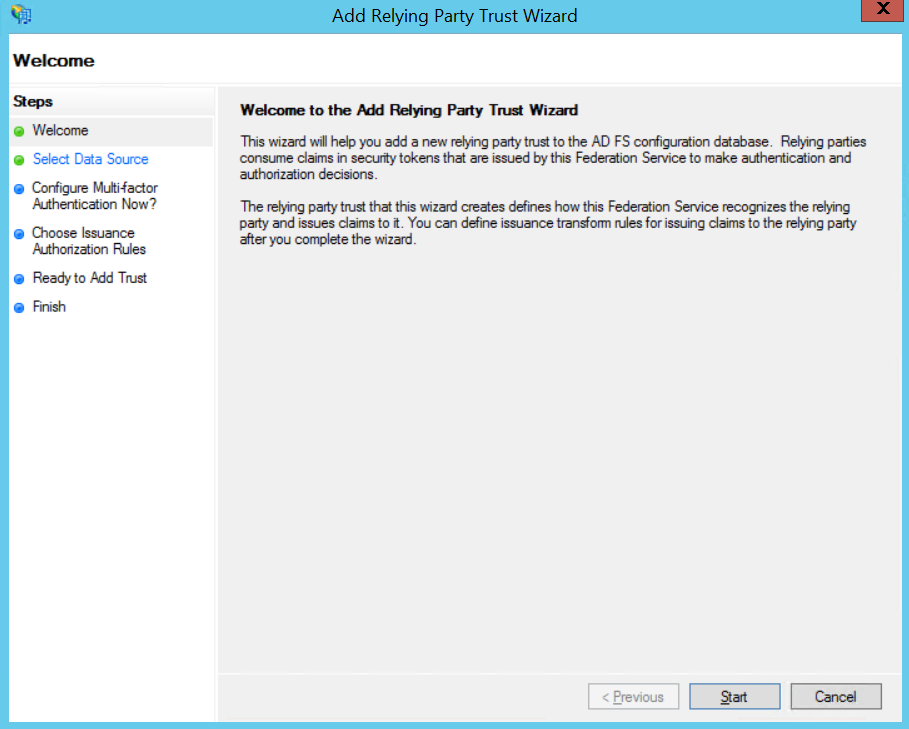
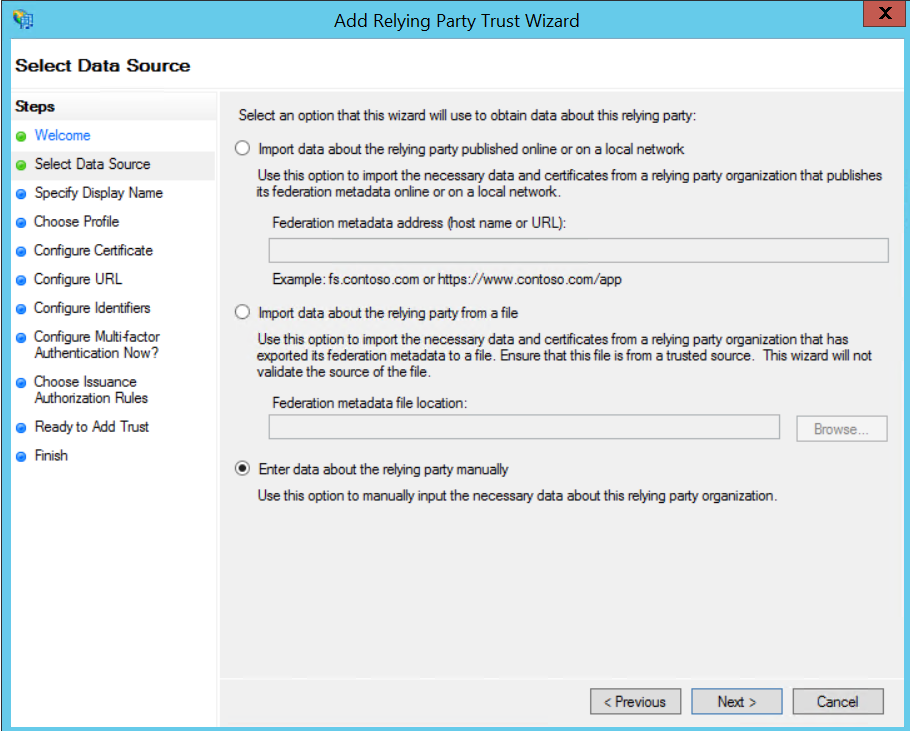
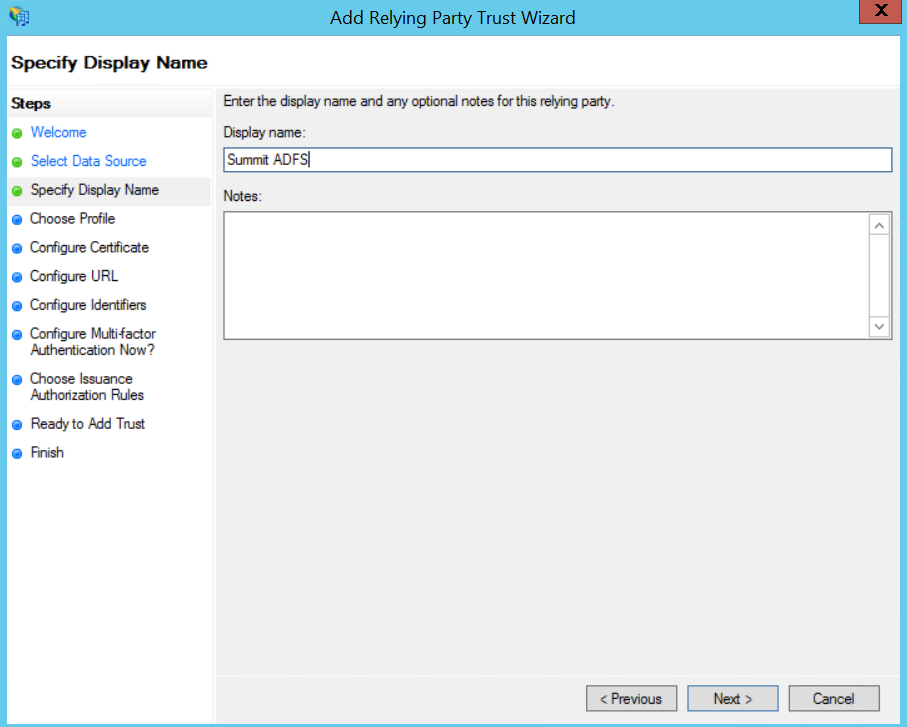

 Configure
Multi-factor Authentication Now
Configure
Multi-factor Authentication Now
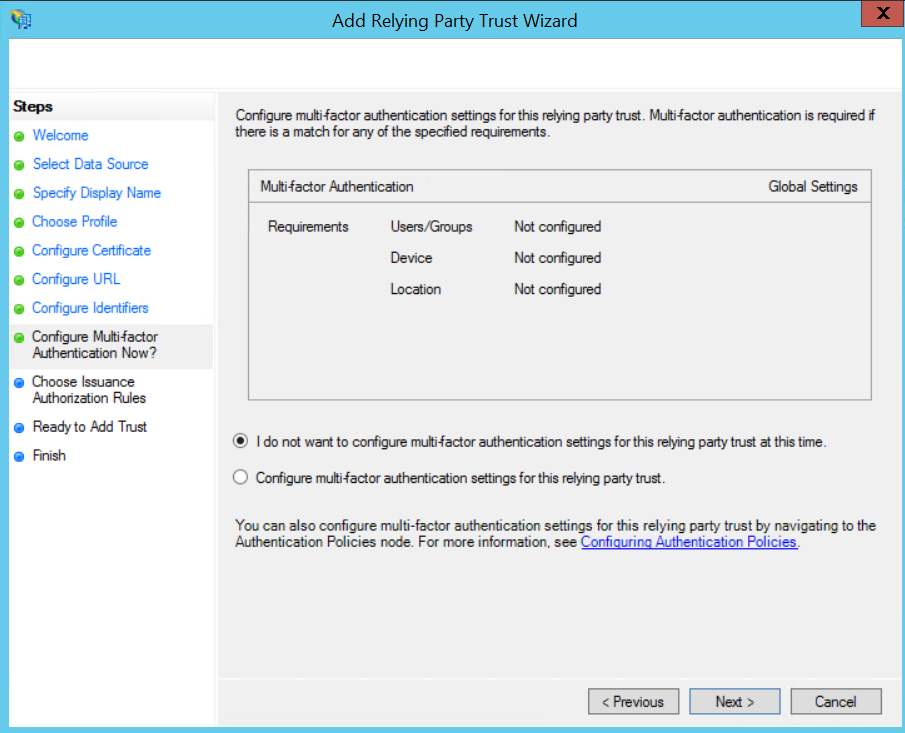
Figure: Configure Multi-factor Authentication Now

 Choose
Issuance Authorization Rules
Choose
Issuance Authorization Rules
Figure: Choose Issuance Authorization Rules tab

 Ready
to Add Trust
Ready
to Add Trust
Figure: Ready to Add Trust tab

 Finish
Finish
Figure: Finish tab
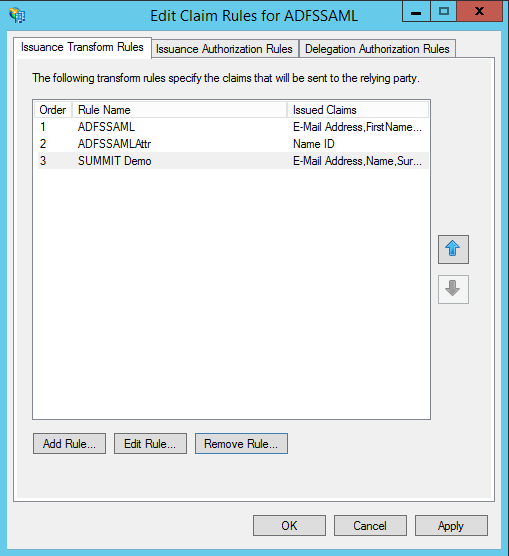

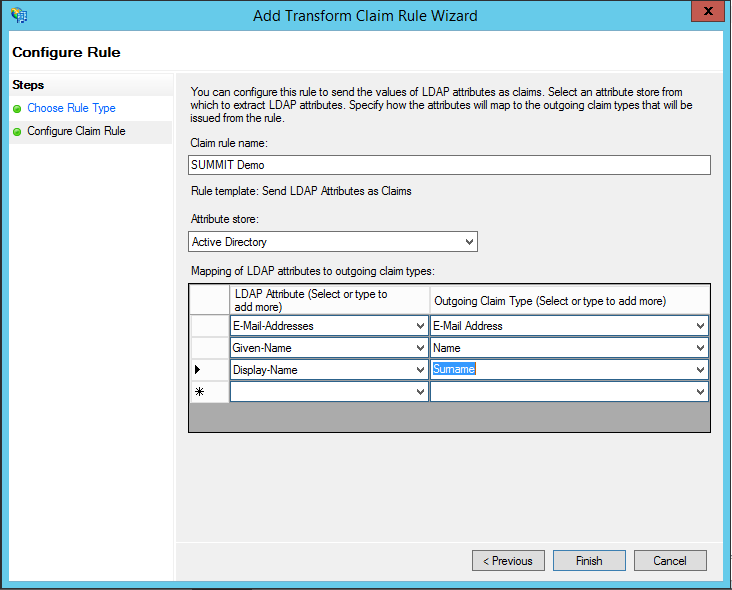
| Note: SUMMIT Application uses Email of the user as a login ID. For this to work, you need to set up the Email as the NameID on the SAML login request. This can be achieved by setting up a Transform Rule. |
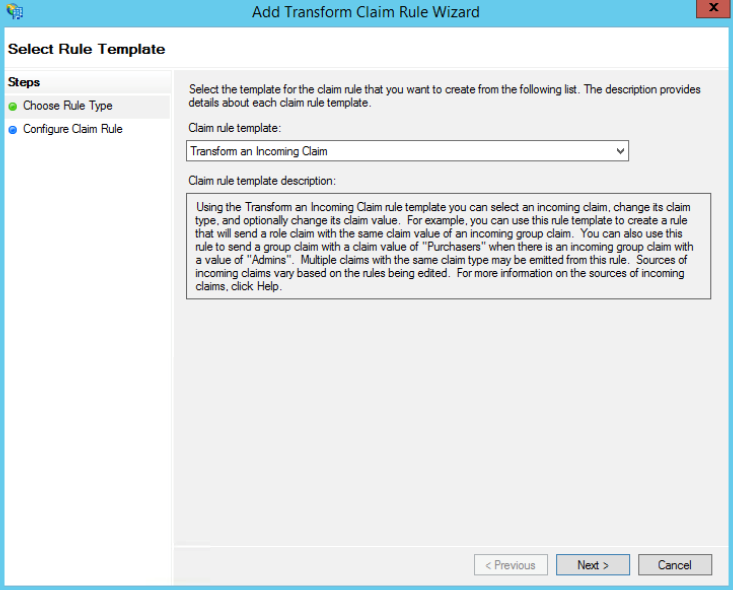
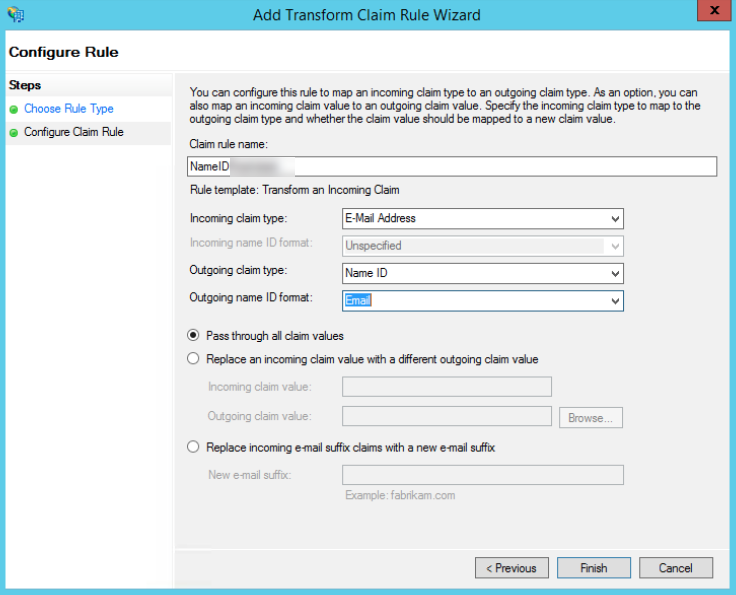
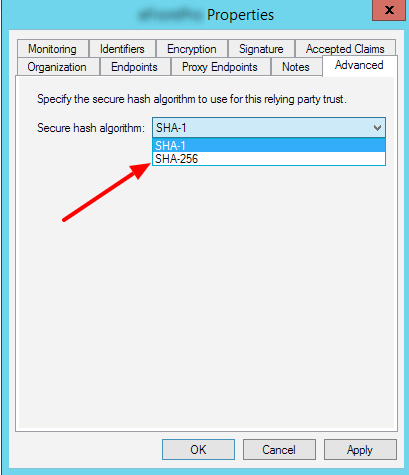
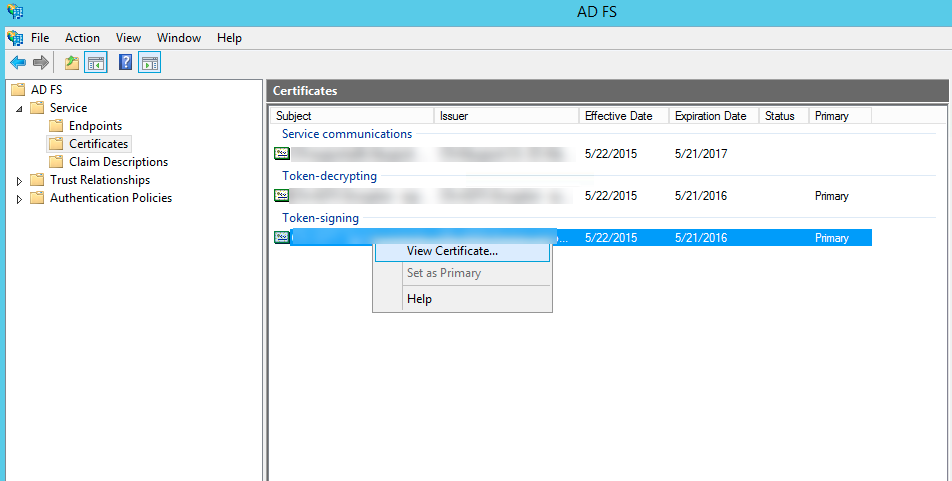
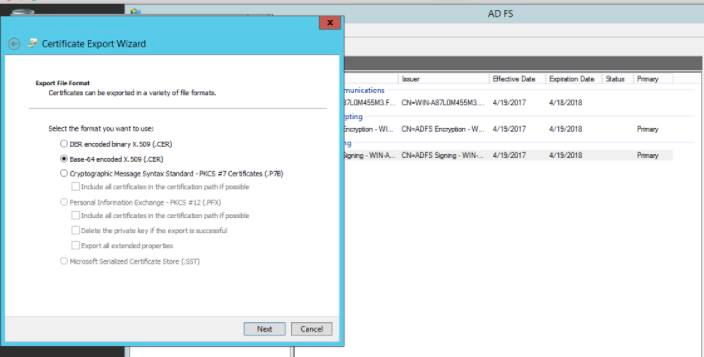

 Configuration
in SUMMIT Application
Configuration
in SUMMIT Application
To configure SSO in the SUMMIT application:
Select Admin > Basic > Infrastructure > SSO Configuration. The SSO CONFIGURATION page is displayed. Select SAML and click ADD NEW under ACTIONS panel.

Figure: SSO Configuration page
Type in the SSO configuration details. For more information about the fields on the SSO CONFIGURATION page, see Field Description.
Click VALIDATE. The certificate information is displayed if the uploaded certificate is valid. For invalid certificate, an error message is displayed.
Click SUBMIT. The SSO is configured successfully.
The following table describes the fields on the SSO CONFIGURATION page:
| Field | Description |
| URL | Provide the URL. |
| Redirect URL | Copy the SSO URL details from ADFS configuration page and paste the URL details in this text box. |
| SSO Type | Select the SSO Type from the drop-down list. |
| Response Attribute | Select the response attribute from the drop-down list. |
| Upload Certificate | Upload the certificate that you downloaded during the SSO configuration using ADFS SAML apps. |
| Logo | Upload an image to be displayed as ADFS icon. |
This section explains all the icons displayed on the ACTIONS panel of the SSO CONFIGURATION page.
SHOW LIST
Click SHOW LIST to display the LIST table showing the SSO configured in the SUMMIT application for Okta.
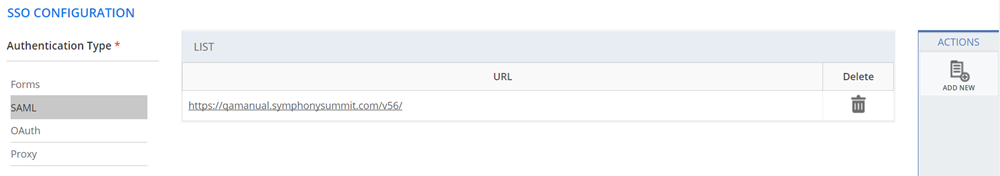
Figure: SSO Configuration : SAML
Published on 21st September 2018, v5.7 SP2
© 2018 SUMMIT Software Inc. All Rights Reserved.